ERPs and other enterprise business applications play a significant role in a company’s architecture and business processes. Unfortunately, these systems may easily fall victim to cyberattacks.
What is ERP?
ERP is Enterprise Resource Planning System. As you can understand from this acronym, this system is responsible for managing all company’s resources. Many years ago, people used to store all information about employees, materials, products, clients, etc. on the paper, then, Excel spreadsheets were used, but later when the number of employees involved in business processes increased and the need for automation grew significantly, we met ERP systems. Those systems now store and process all the “crown jewels” of a company, however, they also pose a huge risk if not secured properly.
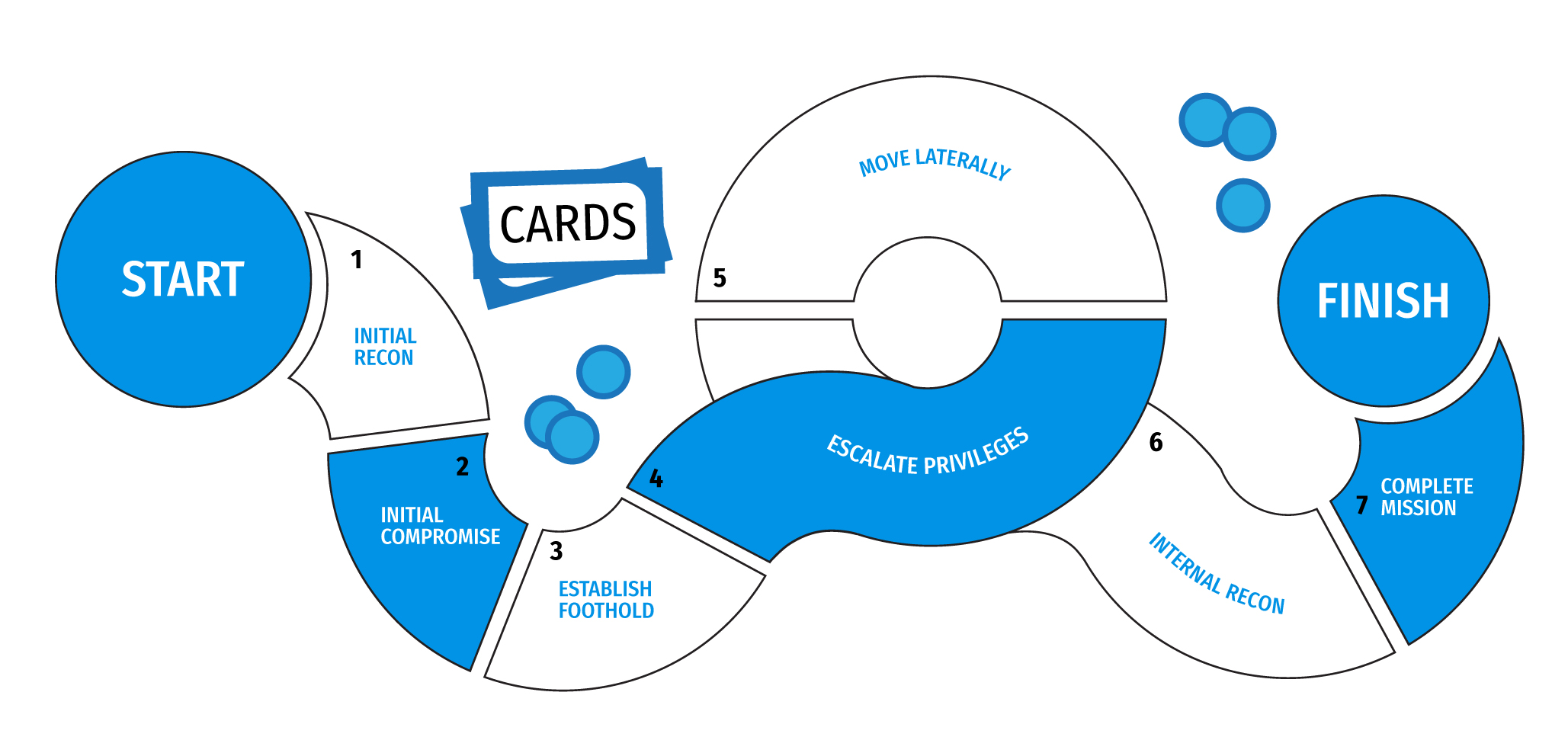
A typical cyber kill chain consists of multiple steps such as initial reconnaissance, initial compromise, establishing foothold, escalating privileges, gaining access to the mission-critical system, internal recon, and, finally, stealing the data or changing some critical configuration parameters.
There are plenty of security solutions (Firewalls, WAFs, endpoint protection systems, etc.) intended to detect or even prevent initial intrusions. They are mostly focused on the first stages of an attack, but some of them can aid as well when an attacker is already inside the system.
Every year we witness more and more data breaches while most victim companies have common security mechanisms implemented. It seems to suggest that getting access to a corporate network is not a difficult task for skilled attackers. In my opinion, this situation will not change in the near future, as if something is valuable, someone will try to steal it.
So, the most reasonable strategy is to protect the most critical assets, and it is completely different task comparing to boundaries protection.
Imagine our network is a castle. The security measures are implemented: here is a moat swarming with crocodiles, castle ramparts, and towers with guards. It seems secure. However, if a mole digs a tunnel under the castle walls and gets inside, the intruder will get access to the treasure because there are almost no security equipment inside the castle.
As a conclusion, it is obvious that we should focus at least on the following areas of cybersecurity:
- Network security
- Web Application security
- Endpoint security
- Identity and access governance
- Incident detection and response
- Business application security
The last topic deserves greater attention, as it is responsible for business critical processes. To tell the truth, all our networks, web applications, endpoints, and identity systems are here mostly to provide access to those business applications such as ERP systems. Without them, all IT infrastructure features turn out to be almost useless.
There are different ERP Systems available on the market. The most common systems are SAP ECC, Oracle EBS, Oracle JDE, Microsoft Dynamics, Infor, etc. Despite the fact they are different in details, they are quite similar in general and represent a 3-tier architecture consisting of fat client or web browser, application server or multiple application servers with a load balancer, and a database as a backend.
Why should we care?
What can happen if somebody breaks into the most critical assets such as ERP as well as SCM (Supply Chain Management), PLM (Product lifecycle management)?
Espionage (breach of confidentiality) includes theft of financial information, corporate trade secret, Intellectual property and customer data.
Sabotage (violation of availability) can be in form of intentional product quality deterioration, production spoilage, equipment corruption, manipulation with supply chain, compliance violations, and tampering with financial reports.
Fraud (violation of integrity).There are different kinds of fraud, which can relate to row materials, finished goods, financials, etc. Finally, terrorism (such as explosion) now is also among the cybersecurity risks. All this can happen because of a single vulnerability in ERP System.
There are different ERP Systems available on the market. The most common systems are SAP ECC, Oracle EBS, Oracle JDE, Microsoft Dynamics, Infor, etc. Despite the fact they are different in details, they are quite similar in general and represent a 3-tier architecture consisting of fat client or web browser, application server or multiple application servers with a load balancer, and a database as a backend.
What’s more important, they vary from traditional applications in the following options:
Complexity. As a rule, complexity kills security. Just imagine, ERP system from SAP (238 Million lines of code as for 2007) contains more source code strings than Windows 7 + Mac OS Tiger + Debian 5 all together ( 85+ 65 + 40 million lines of code ). So, there may be many different vulnerabilities at all levels, from network to application. (http://www.informationisbeautiful.net/visualizations/million-lines-of-code/)
Customization. Every business application such as ERP is more like a framework, on top of which customers develop their own applications on a specific language. For example, programmers use the ABAP language to extend functionality of SAP System while for applications such as Oracle PeopleSoft they use the PeopleCode language;and the X+ language are used in Microsoft Dynamics to customize it.
Criticality. This software is rarely updated, as administrators are scared the systems can be broken during updates due to backward compatibility and connection with legacy systems. Sometimes instances of SAP systems being not updated for several years even occur. (http://news.softpedia.com/news/five-year-old-sap-vulnerability-affects-over-500-companies-not-36-504043.shtml)
Closed nature. ERP systems are mostly available inside the company that is why business applications are considered a closed world. Very few security experts have access to them and spend their time to study these systems.
In next article we will tell about typical attacks vectors on SAP systems.
