Let's imagine a situation when cyber-attacker executes some commands remotely on the infected workstation using command line interface (cmd.exe) or using a special USB-device like Teensy or Rubber Ducky

How can we see these commands during digital forensics process?
In this test case I've used a typical USB-Rubber Ducky device with payload which is being executed starts a command line console (cmd.exe) and then uses xcopy.exe to copy some data to hard drive. After this I made a RAM dump and tried to find these commands with volatility script. And there are no commands typed with fake keyboard (Rubber Ducky) were found.
Another way you can take — if some console utility was started and you see .pf files related in \Windows\Prefetch folder you can check a memory dump with winhex or another tool to find some instances of this commands inside memory.
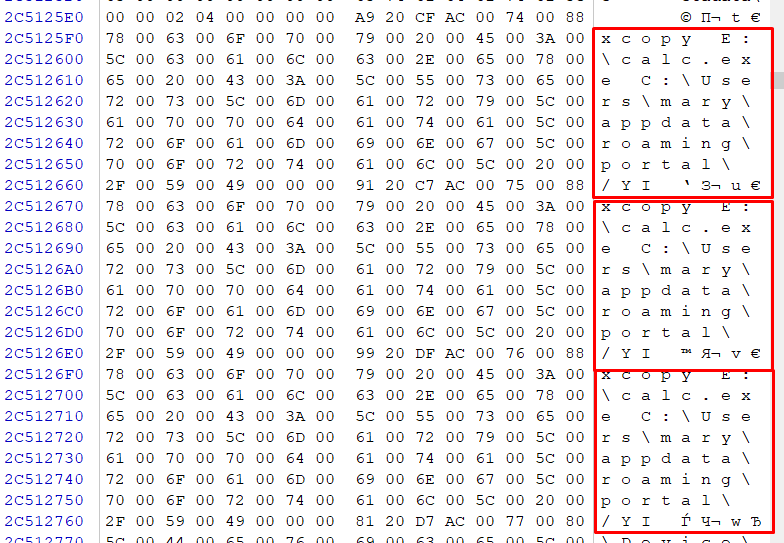
But you obviously need a special skills to make this research and also it can take some time depending of your skills level.
So, if a cyber-attacker uses a kind of Rubber Ducky device or types commands remotely in cmd, it's really hard to find whole text of these commands during incident investigation.
What can we do to be ready for similar situations and to make a corporate IT infrastructure well-prepared for fast digital forensics envestigation?
If your IT infrastructure is built on AD DS and Windows Server 2012 R2 / Windows 8.1 OS, you can configure Enhanced Command-line Auditing via Group Policies.
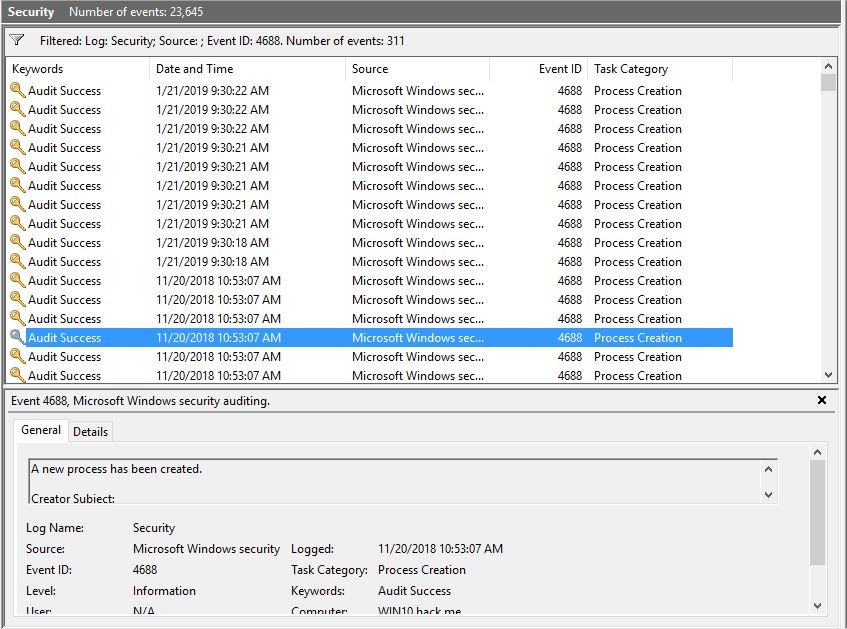
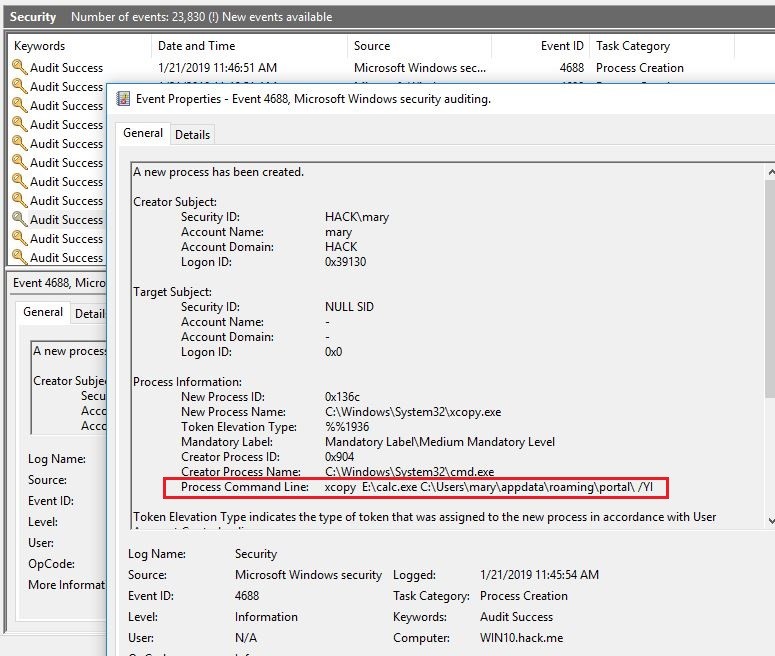
There is a special event ID 4688 in the Windows Security Events, but without additional configuration it includes just scant information about processes and not includes any helpful information about commands typed and executed in command console.
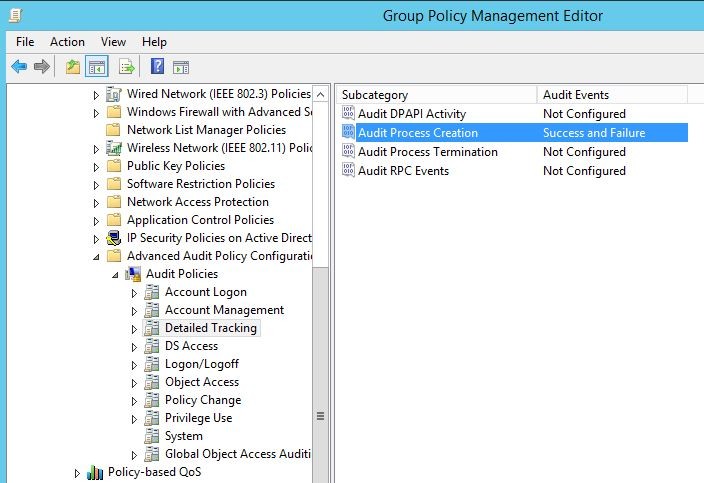
All we need to do is to enable two options in Group Policy object using gpmc.msc on Domain Controller:

Of course it needs to update this policy on the workstations under monitoring using gpupdate /force or just wait for your domain GP update interval.

Now if any commands are executing from command console, they become stored with whole text in system Security events with ID 4688:
Thank you, I'll be back soon with other good Digital Forensics content!

How can we see these commands during digital forensics process?
In this test case I've used a typical USB-Rubber Ducky device with payload which is being executed starts a command line console (cmd.exe) and then uses xcopy.exe to copy some data to hard drive. After this I made a RAM dump and tried to find these commands with volatility script. And there are no commands typed with fake keyboard (Rubber Ducky) were found.

Another way you can take — if some console utility was started and you see .pf files related in \Windows\Prefetch folder you can check a memory dump with winhex or another tool to find some instances of this commands inside memory.

But you obviously need a special skills to make this research and also it can take some time depending of your skills level.
So, if a cyber-attacker uses a kind of Rubber Ducky device or types commands remotely in cmd, it's really hard to find whole text of these commands during incident investigation.
What can we do to be ready for similar situations and to make a corporate IT infrastructure well-prepared for fast digital forensics envestigation?
If your IT infrastructure is built on AD DS and Windows Server 2012 R2 / Windows 8.1 OS, you can configure Enhanced Command-line Auditing via Group Policies.
There is a special event ID 4688 in the Windows Security Events, but without additional configuration it includes just scant information about processes and not includes any helpful information about commands typed and executed in command console.

All we need to do is to enable two options in Group Policy object using gpmc.msc on Domain Controller:
- Computer Configuration\Windows Settings\Security Settings\Advanced Audit Policy Configuration\System Audit Policies\Detailed Tracking\Audit Process Creation

- Computer Configuration\Administrative Templates\System\Audit Process Creation\Include command line in process creation events

Of course it needs to update this policy on the workstations under monitoring using gpupdate /force or just wait for your domain GP update interval.

Now if any commands are executing from command console, they become stored with whole text in system Security events with ID 4688:

Thank you, I'll be back soon with other good Digital Forensics content!
Комментарии (2)

markandy
27.02.2019 13:10I think this is an informative post and it is very useful and knowledgeable. therefore, I would like to thank you for the efforts you have made in writing this article.
Arcade Games


LevonTerGhazaryan
I like your report :) Thank you