Smoothly the era of mesh-networks is upon us. At the very least, the term is appearing more and more often in the information sphere. What attracts the attention of networkers? Let's try to understand the question, taking Yggdrasil network as an example as one of the most promising prototypes.
The general idea of topology
The Internet, like any other network, such as a local network of several computers, is a network of connected computers. The order in which the devices are connected in the network is called the topology and is determined purely by the preferences and capabilities of the administrator. At home you may have a Wi-Fi access point for easy connection from a smartphone and a couple of desktop computers connected to the router with a cable. Obviously the order in which you connect your laptop to the Internet in your apartment is up to you. There is no single and obligatory configuration, but any solution has its pros and cons.

As you can see in the illustration, star topology is the most vulnerable, but it is also the most common in the home because of the ease of organization. You do not need to go far to find an example: you probably have a single switch or router in your home or office, through which all computers are connected to the same local network. If the connecting device is disconnected, all subscribers will be left without communication. The "tree" topology can be considered a logical continuation of the "star": Imagine a building with a separate switch on each floor that connects the offices located on the floor. Because the switches are connected to each other, offices from different floors can communicate. If the switch on the second floor fails, the offices on the other floors can still communicate with each other, but the connection between the first floor and the other floors is lost.
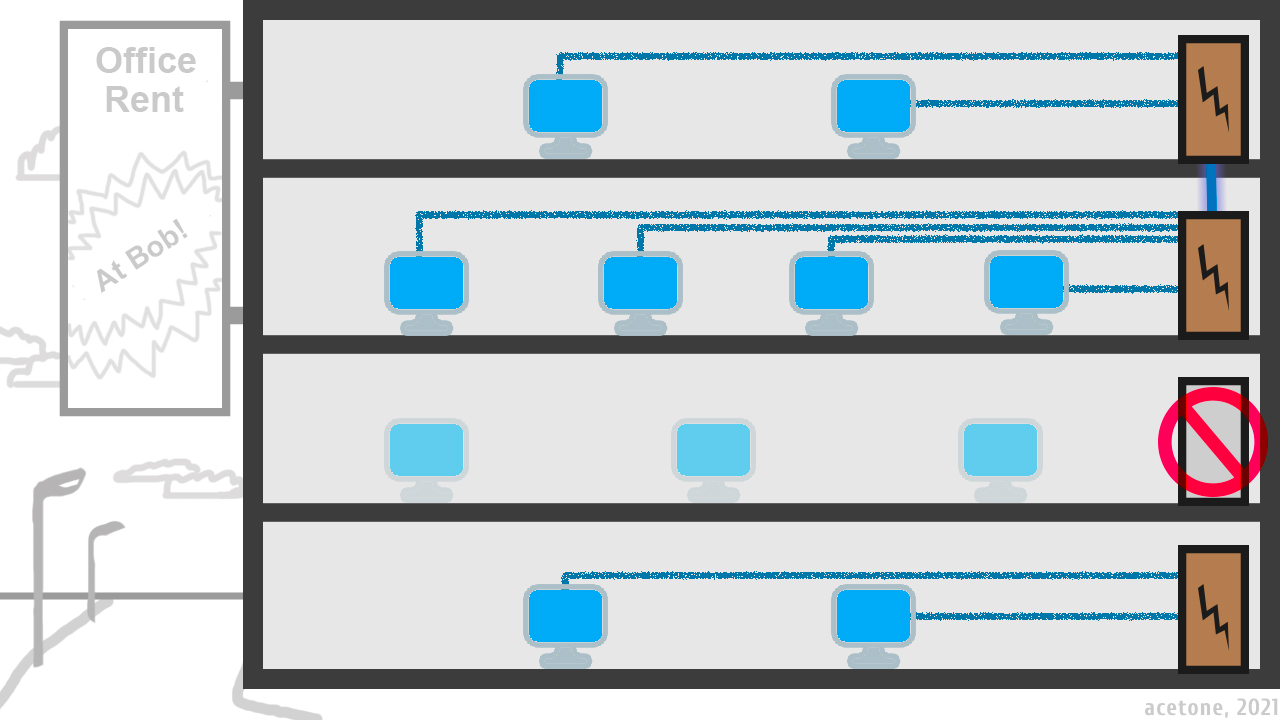
Mesh or "mesh topology" is a network architecture in which all network participants are equal and act both as client and router for other participants. The main advantage of mesh is high fault tolerance and the disadvantage - the complexity of practical implementation. Mesh topology has been widely used for decades, first by the military and second by large businesses. It implies a complex design taking into all possible conditions and is often coupled with radio technologies, because radio is an indispensable assistant in the organization of communications in the field.
Network transmission model
When we were kids, many people wondered about the magic that allows sound and pictures to be transmitted through a thin coaxial cable. Now there are even more questions, because the entire World Wide Web is somehow transmitted wirelessly right into a little box called a smartphone.
Everyone is familiar with the concept of IP-address - a logical address for routing its incoming and outgoing information over the network. Without going into technical details of TCP/IP stack, where IP is easily remembered "Internet Protocol", we should distinguish two main types of IP addresses:
IPv4 - four-byte addresses written in decimal notation and separated bytes by a dot as "192.168.1.10." IPv4 is familiar to the eye and easy to understand, but it has a small address space of about four billion variations. Less than the population of the Earth: you can not give everyone a unique address, let alone the Internet of Things.
IPv6 – hexadecimal bit addresses, written in hexadecimal notation with colons separating every two bytes. It looks something like this: "fe80:2a30:6b30:c26d:3d39:3ce4:218:6376". It is difficult to perceive and remember, but has an infinite number of possible addresses for human imagination. IPv6 address space is enough for many planets, taking into account that each inhabitant will have three coffee machines with a unique address.
IPv6 came later than IPv4 and to this day some software only works over an IPv4 network. This is especially true for old software whose developers have stopped actively developing the product.
To get closer to the representation of digital, i.e. binary information transmission consisting of bits - zeros and ones - you need a basic understanding of the Open Systems Interconnection networking model (or simply OSI). A detailed reference can be found in two clicks if you wish, so I won't rewrite the textbook. From an electrical pulse in the wire to the display of a picture in the browser, there are several logical levels involved and the lower the level, the less power is expended on the client side. As long as the signal goes down the wire, the computer is not connected to it in any way. Then the signal reaches the network card of the device and begins its low-level processing by the network card itself. After this, the information is sent directly to the operating system and its logical processing falls on the main resources of the computer. The highest point of this chain is a client application, such as a browser and a picture in it. The total electrical pulse is converted into bits, then these bits form packets, sent to the browser and assembled into a picture on the user's monitor.
Classic Network
Almost any modern telecommunications network implies the presence of an administrator - a user with authority and responsibility. Administrator establishes connectivity, connects new subscribers, and has the right to censor and limit the network segment under his control in any way. This rule applies to both local networks and the global network - the Internet. In the case of the Internet, we resort to providers who connect us to their network. Small providers use in turn the services of backbone providers; those who connect countries and continents with their cables. The more serious the network, the more people serve it. In addition to the physical connection of different computers by wires, there is tremendous work on the logical configuration of the network - routing. It makes our requests to the other continent fly away within a few tens of milliseconds, because each upstream router knows who needs to pass a packet on. Without a routing setup and a person to set it up, not even a tiny local network of a few offices can do!
In today's global network paradigm centralization has taken root, i.e. control over critical infrastructure by a certain circle of individuals: governments and businesses. Some of them have the right to set prices, others to cut us off from the world altogether. And they all have the power to monitor and regulate user activity. It seems that there is no getting away from this.
Yggdrasil
Has your home router ever failed, leaving everyone in your household without network access? Imagine how nice it would be if the router was not a "bottle neck" and if it failed, everyone in the home network could access the Internet through the smart TV, the neighbors' wireless networks and eventually through your smartphone, all without any additional configuration after the router failed!
All applications are forced to use encryption when transmitting information over the network so that intermediate participants cannot intercept sensitive information. For example, almost all modern websites use the HTTPS protocol, which allows for an encrypted connection between the user and the server. This allows us to safely enter passwords, bank card data and trust that the information we enter will only be received by its intended recipient. Imagine that a network connection is always secure at the protocol level and there is no need to pile on additional security features, including no need for certification authorities - organizations, on the trust of which the whole world uses the already named HTTPS (certification authority is a security point of failure, because it assures us of a secure connection, but can be compromised).
To organize a local network in an enterprise, to set up a VPN for remote employees, even for a small network of three computers requires some level of literacy and an appropriate specialist. But what if there is a solution that allows zero configuration on the side of the average user, while allowing to merge or split local networks with full routing integrity (with physically accessible nodes)?
As you have already understood, all of the above features have been implemented and are actively developing. We got to the main agenda of the article Yggdrasil is a software implementation of a meshed network with absolute scalability, automatic routing and end-to-end encryption of all traffic from user to user. Yggdrasil is a software solution that eliminates the need for an administrator when organizing small and medium-sized networks, and minimizes the impact of crazy lawmakers on network connectivity in general.
Yggdrasil Addressing
Yggdrasil uses IPv6 addressing with the 200::/7 netmask. Addresses from this subnet are not used on the Internet, so there are no collisions. Each user also has its own subnet 300::/64, which allows you to assign shorter addresses to network interfaces, give addresses from this subnet to local users at home, and use them to host multiple resources at different addresses (e.g. sites all using port #80). The short address is automatically routed to the full address from subnet 200::/7, the first 64 bits of which are the same. For example, the address [324:9de3:fea4:f6ac::ace] is routed to the host with the full address [224:9de3:fea4:f6ac:6d7c:68f5:6c8e:f9a9]. Addresses from the user's additional subnet are easy to recognize by the first three in the address, because full addresses always use a two.

The user address is generated when the network software client first starts up. To prevent someone else's address from being assigned, the IPv6 address in Yggdrasil is directly derived from the encryption key. A connection will not be established if the encryption key does not match the IPv6 address. Since picking up or stealing someone else's key is a very non-trivial task, we can conclude that Yggdrasil addresses are immune to malicious attempts to interfere with their use. Read more about the cryptographic formation of IPv6 addresses in Yggdrasil in this article.
Due to the fact that the entire Yggdrasil network, regardless of size and physical location of the nodes, uses the same subnet, it is impossible to conduct global address routing using the canonical network administration tools.
Building a common coordinate tree in Yggdrasil
In traditional networks, where meaningful allocation of allocated addresses occurs, the routing logic is configured by numerous administrators, but how does a network work without an administrator when it has thousands of nodes all over the world? The name Yggdrasil comes from the tree of the same name in Scandinavian mythology, which unites the worlds. The name for the network is not random, because the routing in the network has a tree structure.
In addition to the IP-address, network nodes have coordinates that reflect their logical place in the network. For these coordinates to have a starting point, a certain equal member of the network is selected among the nodes.
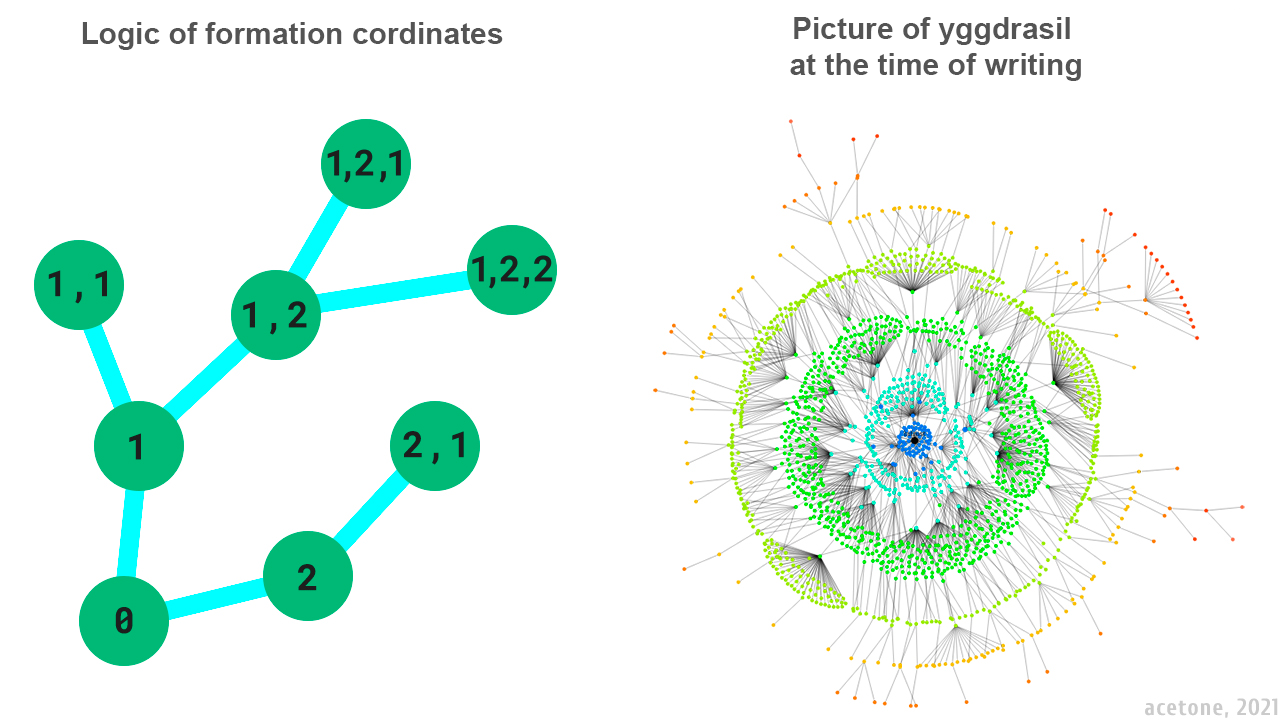
The network map above does not show all node-to-node connections, but only some routes based on the logic of coordinate formation. The impression of centrality is erroneous, because it is not the topology of information transfer, but the scheme of orientation of nodes within the network.
The logic of calculating the zero coordinate node
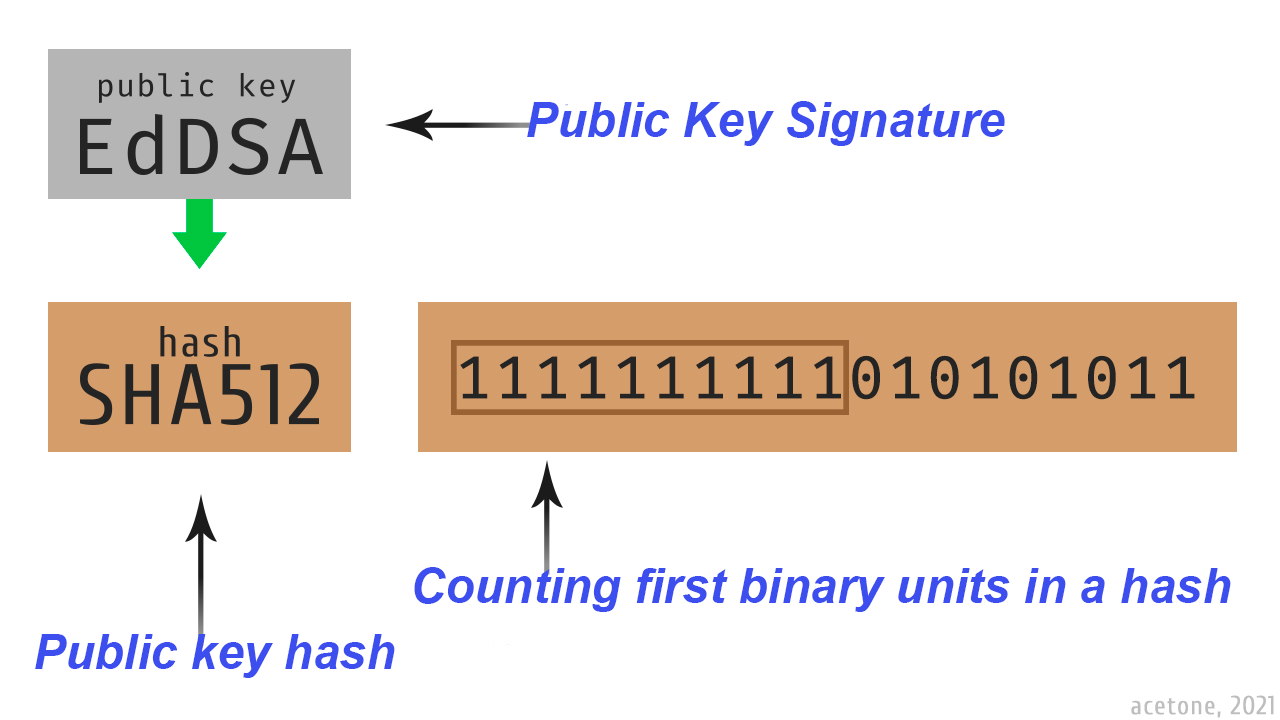
A SHA512 hash is taken from the signature key and the first bits set to one are counted. The node with the highest number of leading units in the hash of the signature key automatically becomes the starter point for the other nodes. When a member with a more suitable key appears in the network, the coordinate tree is rebuilt, counting it as the root.
The first time an address is accessed a broadcast poll of the closest members takes place and then the search request is propagated further across the network. When the request reaches a node that directly sees the target address, a response is returned to the requesting subscriber. The concept of Yggdrasil is based on the shortest possible paths and the fastest possible rate of information transfer. In contrast to the first request, the established session between the two participants in most cases is carried out on the same route, based on the coordinates of the transit nodes. Because of this specificity, the first response has the longest latency and when the session is established and the optimal route is determined, the delay stabilizes.

The most notable bug, eclipsing all other possible lesser flaws, is "network storms". Threat model consists of an impulsive appearance and disappearance of the node with the signature key, which forces the other participants to rebuild the coordinates, taking him as a reference point. As you can easily guess, if the coordinates are constantly rebuilt, network routing suffers greatly, up to complete loss of pings.
Experience and theory of using Yggdrasil in production
The first release on GitHub is dated February 17, 2018. However, to this day, Yggdrasil is positioned as a "raw" product, a beta and is not recommended for use in serious projects.
Many threats of network instability are relevant only when connected to the global segment of the network, where much of what happens does not depend on us in any way. In the case of business solutions, there are cases where remote employees, such as accountants, are successfully connected via Yggdrasil: RDP without excessive router configuration and port forwarding. Such networks are organized in an isolated manner, so they are not subject to "network storms": a public peer is organized on the server controlled by the staff sysadmin, to which all employees are connected in overlay mode (i.e. via the Internet). The result is an easily scalable network like a VPN with an internal IPv6. Yggdrasil can also be used to route local IPv4 networks the configuration file has the corresponding parameters.
Yggdrasil has a built-in means of restricting access to the operating system's network interface, allowing only a trusted list of keys, which are specified in the configuration file. Thus, only manually added users will be able to connect to the TUN interface of the machine. Untrusted network members will not even be able to ping such an IPv6-Yggdrasil, and the transit traffic on the host will not be affected in any way.
Also, since version 0.3.15 Yggdrasil allows you not only to block or allow some addresses, but also to specify encryption keys and signatures when configuring a connection to a public peer. In case of centralized connection of employees in an organization to some public peer, this option is more relevant than ever, since it prevents from a theoretical attack in the form of IPv6 address spoofing due to direct key manipulation.
Technical notes
Yggdrasil works at a very high network layer (L3) by creating its tunnels on top of regular TCP/IP. All processing of intranet traffic requires computing resources of the operating system. This is mainly related to cryptography: Yggdrasil performs cryptographic operations on the service before passing information to the virtual network interface, which will be accepted by the operating system as normal traffic. With a lot of passing traffic on weak hardware braking can occur.
In order to work in a local network, i.e. to automatically detect peers, it is necessary to enable IPv6 on the actual network interfaces of the computer. On systems without IPv6 support (e.g. Windows XP), you can only connect to Yggdrasil by specifying the IPv4 address of a public peer (the address can be local).
The network scales automatically: if one user in an isolated network segment adds a public IPv4 peak, the entire segment becomes part of the global Yggdrasil network.
Start to use
Detailed instructions, the list of public peers as well as a list of known intranet services can be found on the project's official page. The network client is cross-platform. At the moment of publication, all popular operating systems are supported: Windows, Linux, MacOS, IOS and Android.
To connect to the global segment of Yggdrasil, you need to specify in the configuration file public peers, the list of which can be found at the link above under "Public peers". After a successful start, visit the Russian-speaking community intranet guide: http://[300:529f:150c:eafe::6]. It's like Wikipedia, only inside Yggdrasil and contains a lot of practical tutorials and background information on the topic.
Yggdrasil will be of interest to networking enthusiasts and administrators as well as to the younger generation, e.g. for playing Minecraft on a pseudo LAN (as a replacement for Hamachi).
P.S.
In the early 2010s, the word "cryptocurrency" was almost unknown: somewhere it sounded like science fiction and somewhere it sounded like nonsense. Only small group of people knew what it was all about and even smaller one began to actively get acquainted with bitcoin. Now all sorts of cryptocurrencies are in bulk and the hype train has already moved and jumping into the last car is not an easy and cheap thing to do.
When you hear about mesh-networks, you will realize with a pleasant satisfaction that this train hasn't left without you.
English translate from Russian provided by Vlad Lagemeet.

